Objective:
Design, implement and operate integrated ICT solutions within and across the city based on Edge-to-Cloud orchestration for building/developing software services in Smart Cities focusing on privacy-preserving and modern ICT technologies.
Challenge:
The rapid development of Smart Cities is aided by the convergence of information and communication technologies (ICT). Data is a key component of Smart City applications as well as a serious concern. Data is the critical factor that drives the whole development life-cycle in most Smart City use-cases, according to an exhaustive examination of several Smart City use-cases. On the other hand, mishandling data can severely affect programs with incorrect data and users whose privacy may be compromised. As a result, we believe that an integrated ICT solution in Smart Cities is a key challenge to achieving the highest scalability, data integrity, and secrecy levels within and across Smart Cities.
Introduction:
Benefiting from recent advances in distributed systems, networking and IoT, Smart Cities are expected
to enhance the quality of life of urban citizens and propel cities toward a more sustainable future. The
availability of a variety of IoT is actively contributing to the development of Smart Cities, but the tremendous
amount of data that needs to be generated, curated, classified, analyzed, and transferred to provide
context-aware real-time services to inhabitants creates specific challenges (Allam and Dhunny, 2019; Lee
et al., 2020). Scalable ICT infrastructure management, successful monetisation of data, applications and
computing resources, and the development of hybrid privacy-enhancing technologies are three critical
criteria for developing advanced privacy-preserving Smart City ecosystems (Bélissent, 2010; Pahuja,
2021). In particular, performing data processing in distant cloud data centers present many limitations in
terms of performance, resilience, energy efficiency and privacy (Perera et al., 2017). Edge and Fog
Computing (Bonomi et al., 2014; Shi and Dustdar, 2016) have emerged as a promising infrastructure
solution for latency-sensitive and geographically distributed applications. By placing many small cloud
points of presence (or cloudlets to the edge of the Internet, Fog/Edge Computing brings the users and their
IoT devices closer to the processing resources. As a result, data transfers are kept to a minimum, reducing
the network latency and saving precious bandwidth. In certain models fog and edge devices have limited
processing capacity (e.g., in the case when Single-Board Computers are used) and cannot support massive
data processing (Ghobaei-Arani et al., 2020); in others models, enterprise-grade servers are geographically
distributed in strategic locations (e.g., in urban areas) to improve cost, scale and reliability without sacrificing
performance (Church et al., 2008; Valancius et al., 2009). Furthermore, the Computing Continuum, by
combining the centralized cloud with servers deployed at the edge of the Internet and in-between (fog),
presents a suitable option for latency-sensitive situation-awareness applications because these are
typically sensitive to network delays and connection instability (Masip-Bruin et al., 2016).
Famous computer scientist Prof John McCarthy envisioned a futuristic computing environment where
processing power, applications, and data might be structured as a public utility and sold through a metered
business model at the dawn of the contemporary computation age. According to Prof John McCarthy, such
an ecosystem might enable scalable access to virtually limitless computer resources as well as a wide
range of IT services (Rajaraman, 2014). Selling processing power, applications, and data eventually
became a reality and a market that is largely dominated by a few large IT companies. As a consequence,
individuals and small/medium businesses face massive obstacles in penetrating this market. More recently,
several independent marketplaces have appeared, considering that open, rule-based, uniformly governed,
and federated marketplaces are required to break free of the current oligopoly (Perera et al., 2015; Maciel
et al., 2019). Nonetheless, a significant issue that remains for any marketplace is providing verified,
reputable, and relevant resources to meet gain the trust of buyers. Because they can ensure the security,
transparency, auditability, and the traceability of all deals and transactions among peers, blockchain
technologies (Johansen, 2018; Rejeb et al., 2020; Waleed et al., 2021) are viewed as a major enabler to
meet the need of decentralized marketplaces.
One of the essential requirements for developing a sustainable Smart City is adaptability, for which
artificial intelligence (AI) and machine learning (ML) technologies can play a significant role (Ullah et al.,
2020). In the context of smart cities and AI, data is one of the most critical components. However, data
raise two significant concerns; firstly, handling data without breaching the privacy of their owners can be
challenging, since it constantly flows from one computing system to another; second, the security and
performance of AI/ML applications can be harmed by fabricated or corrupted data (Li et al., 2017;
Sambasivan et al., 2021; Xu et al., 2021). Therefore, maintaining a high level of security throughout the
whole computing chain is paramount to safeguard the data, and can only be achieved through
comprehensive infrastructure management and auditability (Al Nuaimi et al., 2015). In light of this, three
different main ICT architectural reference models and their related data management and flow architectures
within the Smart City paradigm have been proposed started from Decentralized-to-Centralized (DC2C-ICT)
Sinaeepourfard et al. (2017) to Distributed-to-Centralized (D2C-ICT) (Sinaeepourfard, 2017;
Sinaeepourfard et al., 2020), and hybrid (Sinaeepourfard et al., 2020, 2021; Alamouti et al., 2022) ICT
architectures, as represented in Figure 1. With the help of the proposed three main ICT reference
frameworks, the authors showed how efficiently storing, managing, processing, analyzing data, and
software services management can be done within and across the city/cities within the scope of the Smart
City.
Developing Smart City ICT reference architecture models walks through diverse strategic design views.
Those views explain how the ICT architecture models may connect technologies, organizations, and
information in the unified architecture design (Schieferdecker et al., 2017). As shown in Figure 1, we finally
realize that designing ICT architecture in Smart Cities (Schieferdecker et al., 2017; Sinaeepourfard et al.,
2020) may propose through two different strategic ICT design views from “bottom-top” or “top-bottom.”
Besides developing a robust and sustainable ICT architecture and their data management infrastructure,
building strong data privacy and the security mechanism is essential. Therefore, many technological
innovations have emerged to support hardware-level and software-level data privacy-preserving and
confidential computing to ensure the highest level of data security and privacy. For example, hardware-
based Trusted Execution Environments (TEE) offer an isolated execution environment inside the main
processor for securely executing applications and data even in a compromised system (Valadares et al.,
2021). It ensures that the code and data loaded inside are protected in terms of confidentiality and integrity.
In addition, TEE provides security features such as isolated execution, the integrity of applications running
inside, secure data storage, and key management and cryptographic algorithms as an isolated runtime
environment (Ning et al., 2017). In comparison, technologies like secure multiparty computation,
homomorphic encryption, federated learning, differential privacy, and zero-knowledge proof support
application-level data privacy and security (Danezis et al., 2015). In addition to that, federated learning
(Konečnỳ et al., 2016) enables the facilities to keep the private data to the owners, which helps significantly
reduce the data flow in the Smart City domain and helps to utilize the network resources within the Smart
City paradigm adequately.
Ensuring the highest level of data privacy and security is certainly essential for making a more advanced
and sustainable Smart City. Considering this fact and focusing on the different application scenarios, we
propose an architectural solution for developing a privacy-preserving computation framework for managing
big data within the scope of the Smart City domain.
Edge-to-Cloud orchestration can offer a splendid solution for building Software Services across the city
as well as management of the large-scale IoT in smart cities. With the focus on designing large-scale
software services, we should consider data as the most precious resource for service development in smart
cities. Without data, services cannot be lunched for smart city citizens. Therefore, to build efficient smart
city services, we should consider about large-scale IoT data management architecture from data collection
to data consumption as well as assessment and mitigation cybersecurity threats/risks to validate security
requirements for building software service in the smart city.
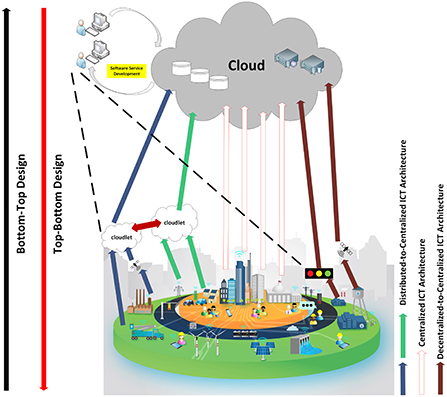
Figure 1. Different ICT architectures in Smart City for data management, processing, and software services development, extract
main idea from Sinaeepourfard (2017), Sinaeepourfard et al. (2020).
References:
Simonet-Boulogne. A, Solberg. A, Sinaeepourfard. A, Roman. D, Perales. F, Ledakis. G, Plakas. I, Sengupta. S, "Toward blockchain-based fog and edge computing for privacy-preserving smart cities," 2022.
